Caosd Research group

vEXgine UMA
Weaving models with CVL and feature models
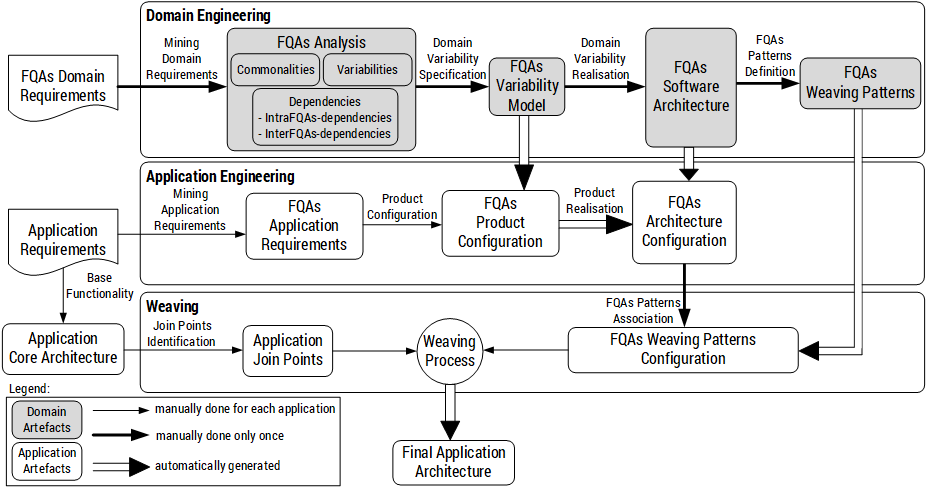
An automatic and generic process for weaving Functional Quality Attributes (FQAs) combining Software Product Line (SPL) techniques and Aspect-Oriented (AO) mechanisms.
Two implementations are compared using different variability and architecture description languages: (i) feature models and an aspect-oriented architecture description language; and (ii) the CVL and an UML.
Modeling green configurations with CVL
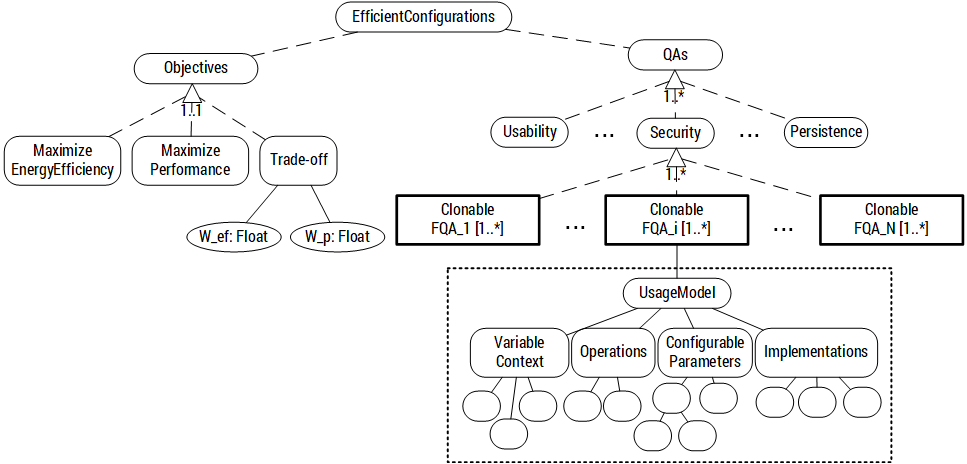
The characterization of quality attributes (QAs) from the point of view of energy efficiency is done with the help of CVL.
CVL models are mapped to a constraint satisfaction problem (CSP) to formally reasoning about energy efficiency and performance and generate the most efficient configurations of QAs.
Injecting Quality Attributes with CVL
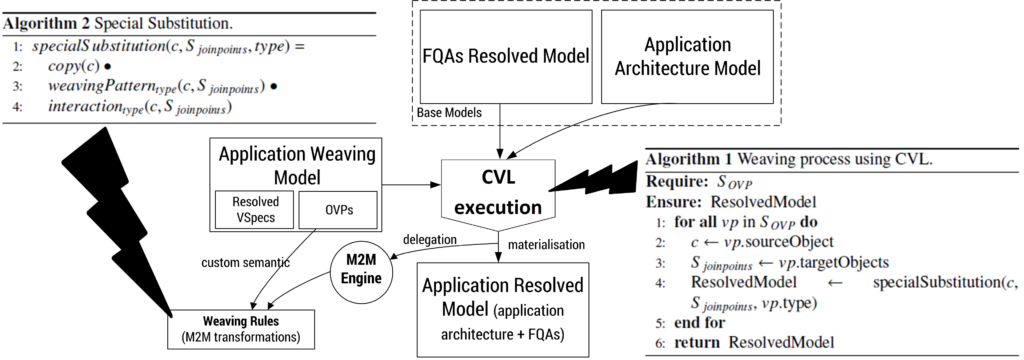
The CVL engine and its delegation engine is exploited to weave models by defining a set of weaving patterns as custom model transformations using Opaque Variation Points (OVPs).
The CVL engine and its delegation engine is exploited to weave models by defining a set of weaving patterns as custom model transformations using Opaque Variation Points (OVPs).
Evolving CVL models
A Product Line Architecture (PLA) approach in which an automatic process for evolving CVL variability and resolution models is defined.
The evolution changes in the CVL models are propagated to the application architecture. CVL variation points and resolution models are formalized following the proposed CVL standard.
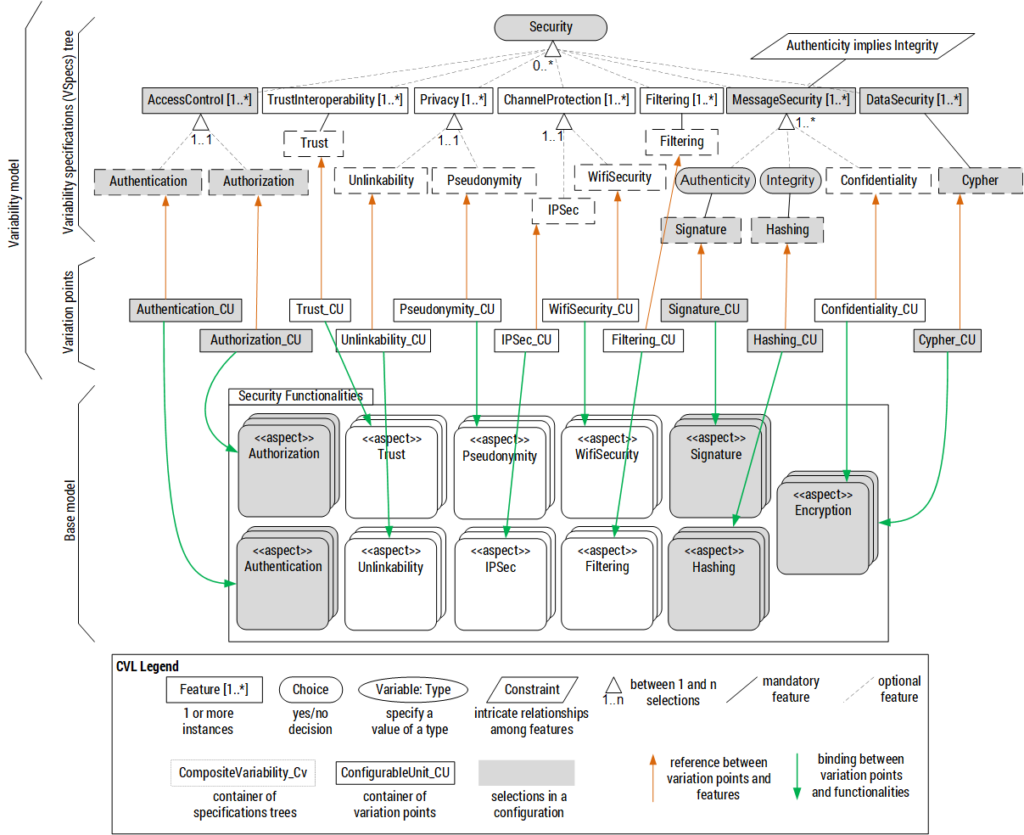
Enforcement of security policies
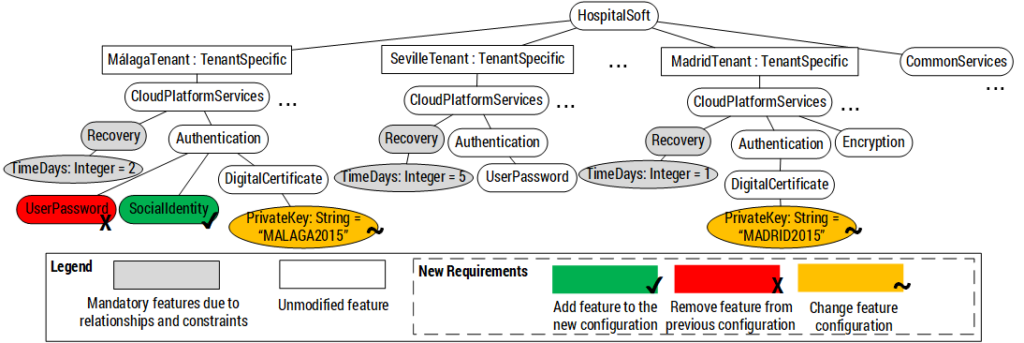
CVL is used to close the gap between the specification and the enforcement of security policies through the deployment of security functionalities (encryption, authentication, hashing,…) within the applications.
CVL allows linking the security policies with the security functionalities and generating a configuration of the security functionalities that fit a security policy.
Moving those CVL models at runtime, the security knowledge can be modeled making use of a Dynamic Software Product Line (DSPL) approach. DSPLs produce software capable of adapting to changes, by means of binding the variation points at runtime.
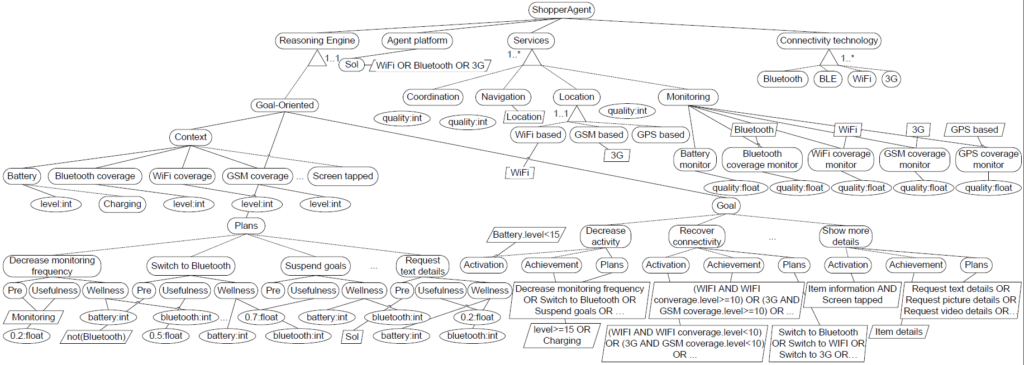
Modeling multi-agent systems with CVL
All the variability present in multi-agent system is modeled in CVL, including the agent cognitive model (goals, plans, context), the agent platform, the services, and the connectivity technology.